Sign up for expert insights, industry trends, and key updates—delivered straight to you.

The consultation focuses on the development of technical standards that will define the requirements for the ICT risk management framework, the classification of ICT-related incidents and the register of information required for all contractual arrangements with third-party providers and the policies governing the use of services by third-party providers.
The ever-increasing dependency of the financial sector on software and digital processes means that information communication technologies (ICT) risks are inherent in the finance sector. As the Commission itself remarked, 'The absence of detailed and comprehensive rules on digital operational resilience at EU level has led to the proliferation of national regulatory initiatives (e.g. on digital operational resilience testing) and supervisory approaches (e.g. addressing ICT third-party dependencies).
DORA will have a significant effect on enhancing the operational resilience of digital environments. By soliciting public input through this consultation process, the European Supervisory Authorities aim to ensure that the resulting technical standards align with industry best practices, promote digital resilience and facilitate robust and secure digital environment across the European Union.
The simplification of the ICT Risk Management Framework
The consultation paper aims to establish a standardised approach for managing risks in information and communication technology across the European Union. By harmonising tools, methods, processes and policies, the EU aims to improve overall ICT and cybersecurity by protecting critical infrastructure and sensitive data. The ESAs have considered the existing European and international standards on ICT risk management, the EBA Guidelines on ICT and security risk management (2019), the NIS2 Directive and the NIST cybersecurity framework components.
The standards set out requirements for all financial entities with respect to:
- Security policies, procedures, protocols and tools for ICT (including governance, risk management, asset management, encryption and cryptography, operations security, network security, project and change management, physical security and information security awareness and training);
- Human resources policy and access control;
- Policies for detecting and responding to incidents;
- Business continuity management;
- Reporting on the ICT risk management framework review; and
- Proportionality approches to managing risks.
New Classification Rules for ICT-related Incidents
The proposed consultation paper requires financial entities to classify ICT-related incidents from other IT-related incidents. Firms will be required to detect and classify incidents and report major incidents and security payment-related incidents to the relevant national component authorities (NCAs).
The proposed mechanism for classification is divided into two categories—primary and secondary. The criteria used between both is defined as follows:
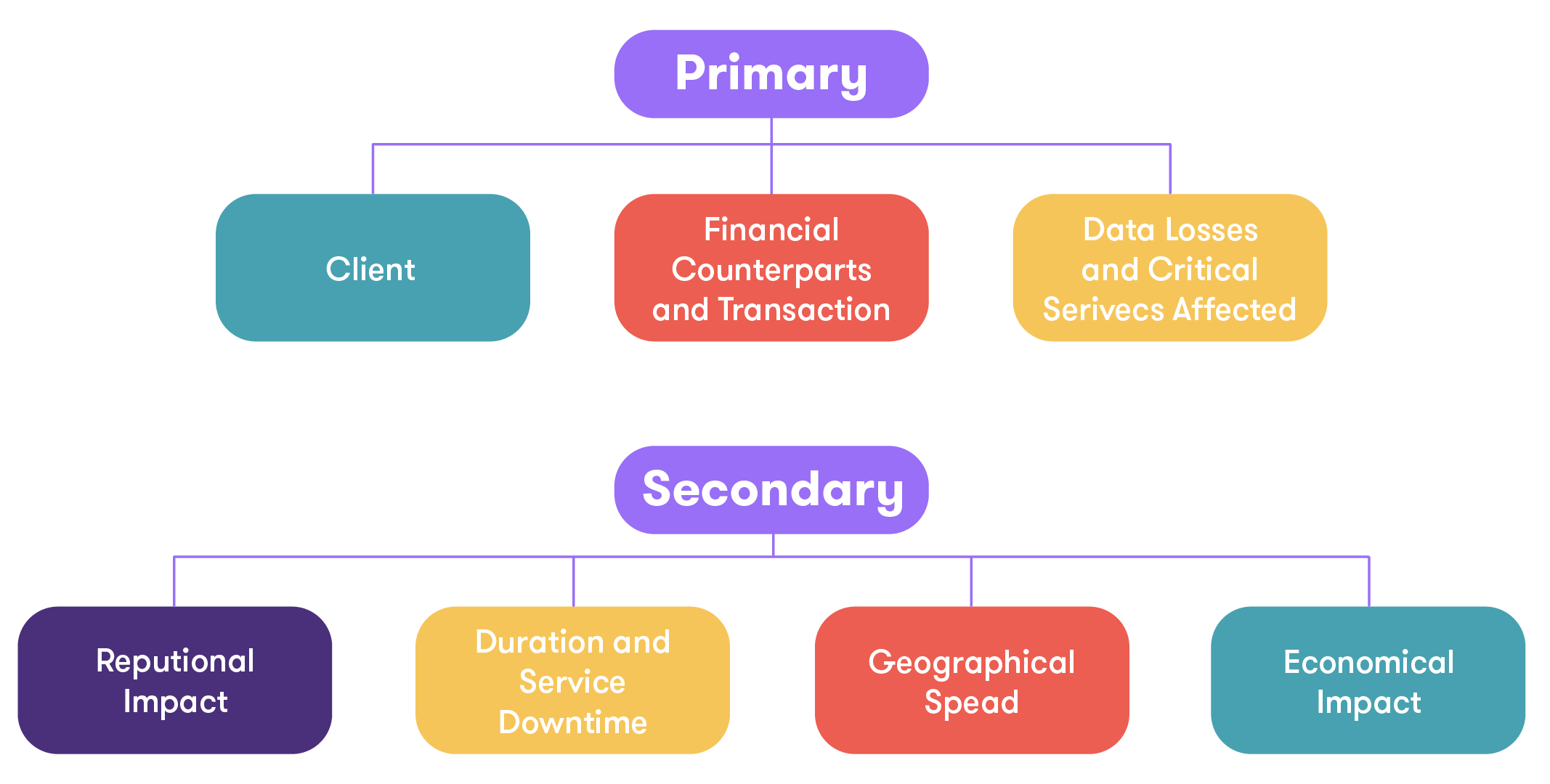
To avoid complexity, the ESAs have discarded the possibility of introducing specific thresholds for cyber threats; instead, they have stated that the classification criteria are the same as those for ICT-related incidents. The consultation paper proposes considering the following elements when assessing the probability of the materialisation of the cyber threat:
- Applicable risks, including potential vulnerabilities of the systems of the financial entity that can be exploited;
- Capabilities and intent of threat actors; and
- The persistence of the threat and any accrued knowledge about ICT- related incidents that have impacted the financial entity.
The ESAs have asked for a response to a number questions including:
- Do you agree with the overall approach for classification of major incidents as illustrated above?
- Do you agree with the approach for classification of significant cyber threats?
Register of Information Required for Contractual Arrangements
DORA requires that at the entity level, firms maintain and update a register of information in relation to all contractual arrangements on the use of ICT services provided by third-party service providers (ICT TPPs). The ESAs have provided register templates to capture risks stemming from the contractual arrangement, the critical or important functions supported by ICT TPPs, the service supply chain with a focus on subcontractors supporting an important function or material parts thereof and the Legal Entity Identifier code of the ICT TPP.
The consultation paper outlines templates for the register of information to be maintained at entity level and sub-consolidated and consolidated level. The templates capture information each of the areas depicted below.
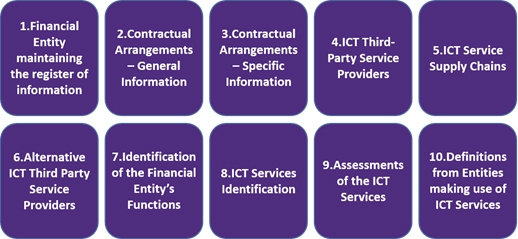
*Source: Consultation Paper on draft Implementing Technical Standards to establish the templates composing the register of information in relation to all contractual arrangements on the use of ICT services provided by ICT third-party service providers as mandated by Regulation (EU) 2022/2554
DORA requires that financial entities must have the established capability to provide the registers to the competent authorities in accordance with the requested uniform formats and using the defined secure electronic channels.
The ESAs have asked for responses on a number of questions including:
- Is the structure of the Register of Information clear?
- Do you agree with the level of information requested in the Register of Information templates?
- Do you think that the minimum level of information requested is sufficient to fulfill the three purposes of the Register of Information, while also considering the varying levels of granularity and maturity among different financial entities?
Policy on ICT Services Performed by Third-parties
This consultation paper provides further detail on the requirement under DORA to maintain a strategy on ICT third-party risk. The strategy should include a policy on the use of services supporting critical or important functions provided by third-party service providers, including intragroup ICT providers. The paper considers already existing specifications provided in guidelines on outsourcing arrangements published by the ESAs.
The policy on the use of ICT services supporting critical or important functions provided by third-party service providers must contain a number of elements, including:
- Methodology for determining which ICT services support critical or important functions;
- The lifecycle stages when using services including risk assessment, due diligence and monitoring;
- The process for assessing that the third-party provider has sufficient resources to provide the service;
- Audit and inspection requirements;
- Differentiating process for ICT third-party providers that are authorised or registered by a competent authority in Member State with those registered in a third country;
- Role of intragroup ICT providers for critical or important functions; and
- Exit and termination requirements.
As noted above, DORA sets out core contractual rights in relation to several elements in the performance and termination of contracts with a view to enshrine certain minimum safeguards underpinning the ability of Financial Entities to monitor effectively all risk emerging at ICT third-party level. Some contractual requirements set out in DORA are mandatory and will need to be included in contracts, if not already reflected.
Others take the form of principles and recommendations and may require negotiation between the relevant parties. Early mapping and engagement in this respect will be important. Additionally, parties may wish to consider benchmarking their existing contractual arrangements against relevant requirements set out in DORA, as well as existing standard contractual clauses developed by EU institutions.
The Path Forward
Following the consultation process, the ESAs expect to submit these draft technical standards to the European Commission by 17 January 2024.
A recent survey conducted by Grant Thornton reveals that 62% of Irish companies in the insurance sector have yet to initiate their implementation of DORA.
With the deadline of 17 January 2025 rapidly approaching, these firms must assess the impact of DORA’s technical standards and begin to take remediation steps.
Taking a risk-based approach reflective of an organization’s size, nature, scale and the complexity of services and operations, Financial Entities should begin to scope out the impact of DORA on their business.
Firms should carry out a comprehensive gap analysis of their existing ICT-risk management processes against the new requirements introduced by DORA to identify any aspects of their existing processes that will be impacted by the new requirements and develop detailed implementation plans setting out the steps that will need to be taken to effect relevant changes. In anticipation of the final publication of the consultation papers, firms can take the following proactive steps to prepare:
- Evaluate your current ICT Risk Management Framework by conducting an comprehensive maturity review on where enhancements and alignments can be made;
- Perform gap analysis of your ICT incident response capabilities with a focus on classification; and
- Revisit your strategy, documentation and approach for third-party service providers with a focus on oversight and monitoring of those that support critical or important functions.
How Grant Thornton Can Help
At Grant Thornton, our commitment goes beyond providing exceptional operational resilience services. We take a partnership approach, working closely with organizations to understand their unique challenges and goals. Don't let the implementation of the Digital Operational Resilience Act catch you off guard. Our team of experts will collaborate with you to develop customized strategies and practical solutions that align with your business objectives. With our comprehensive support, you can confidently tackle the complexities of the Digital Operational Resilience Act while unlocking opportunities for growth and innovation. Contact our Digital Risk team today to embark on this transformative partnership.

